31/12/2019
Digital security in industry – Vulnerabilities in industrial control systems
With the digital revolution in society, security concerns are becoming increasingly prominent. Digitalisation remains, however, an opportunity above all else. This article briefly introduces Digital Security Theory and presents SAFESCAN, a digital security vulnerability assessment process that can identify vulnerabilities in industrial control systems (ICS).
Digital security can increase the availability of industrial automation equipment. In addition, data integrity (data is unchanged) and confidentiality are considered. In ICS systems, availability is paramount. Other security attributes include non-repudiation (proven imprint) and authentication (identity verification). Other basic concepts are threats, risk and vulnerability.
A threat can infiltrate a system with a particular risk. The threat can be an internal or external threat to the company and, for example, vandalism, crime, espionage, terrorism or war. The vulnerability could be caused by people, company processes, or the technology used. In all cases, the risk remains (residual risk), but the company should assess whether the residual risk is acceptable. The risk may be related, among others, to value or reputation. The risk can also be insured as needed to reduce the risk to value, but the residual risk to reputation is more difficult to deal with.
Differences between IT and ICS systems
There are many differences between information technology (IT) and ICS system security and how they are defined. For this reason, it is important that ICS security is defined by a specialist. The person should have know-how of electrical, instrumentation and automation equipment.
Digital security also involves the relationship of the digital device to the physical environment; among others, the location and locking of automation cabinets. However, it must be remembered that the most important security attribute in ICS security is availability, i.e. usability. It may not be possible to lock lockers or devices with locks or passwords if the availability requirement is high. Table 1 lists some of the differences between IT and ICS systems.
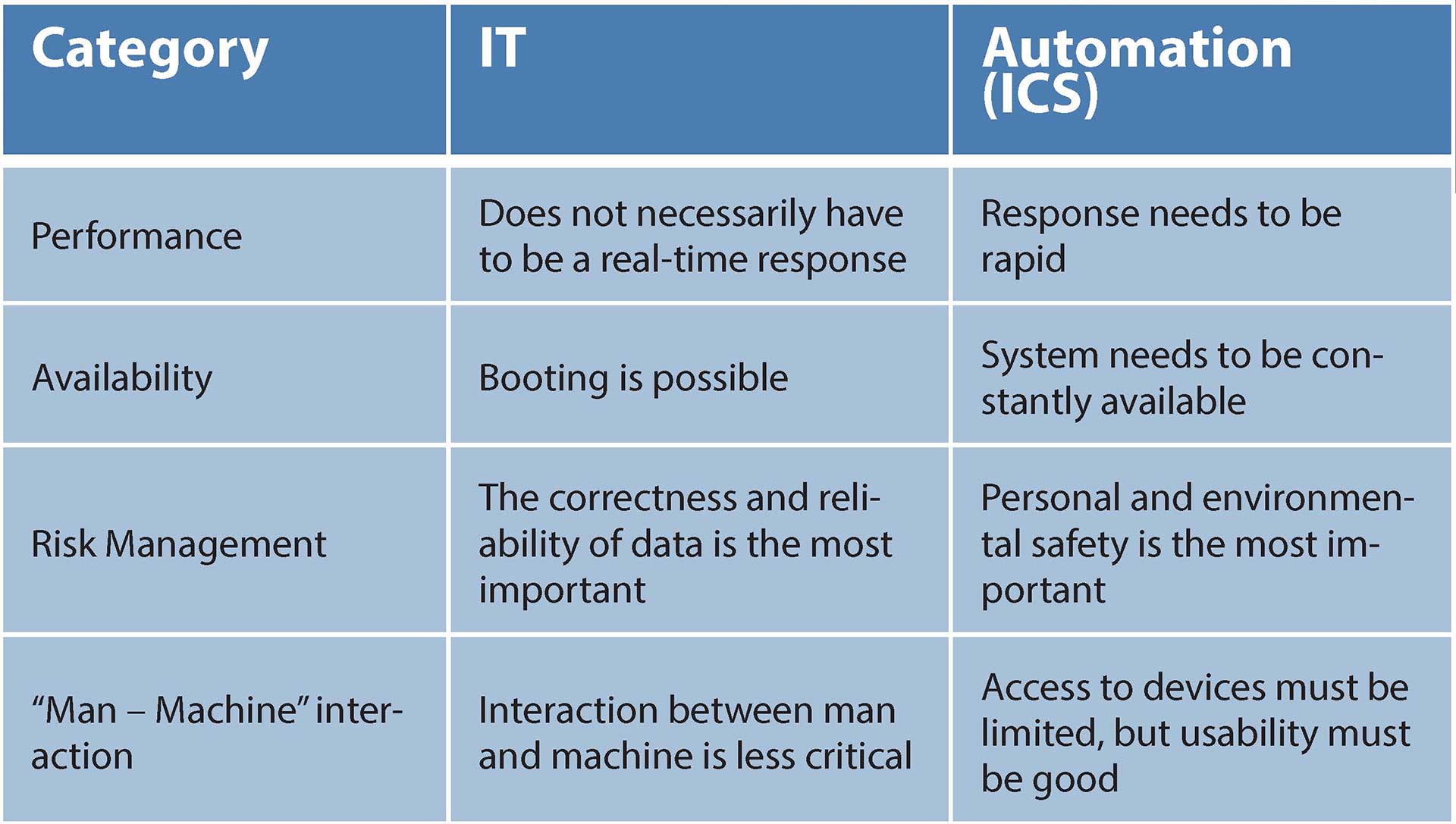
Table 1. Examples of differences between ICS and IT systems.
Security layers of the automation system
Layering should be taken into account in system structure design as it reduces the risk of a successful attack. The automation system is usually isolated from the IT network, for example, with the use of a firewall or demilitarised zone (DMZ). In this case, the connection to the automation network is limited. Systems can often also be accessed remotely via a virtual private network (VPN).
Remote connectivity solutions are provided by various device vendors. In digital security, interfaces pose the greatest risk. Automation systems can be divided into different layers, the outermost layer being the periphery of the network and the innermost level being the data in computers and in the network. The data may be in use, in motion, or stored (stationary). Digital security solutions can be created at these various levels, such as a DMZ or IDS (Intrusion Detection System).
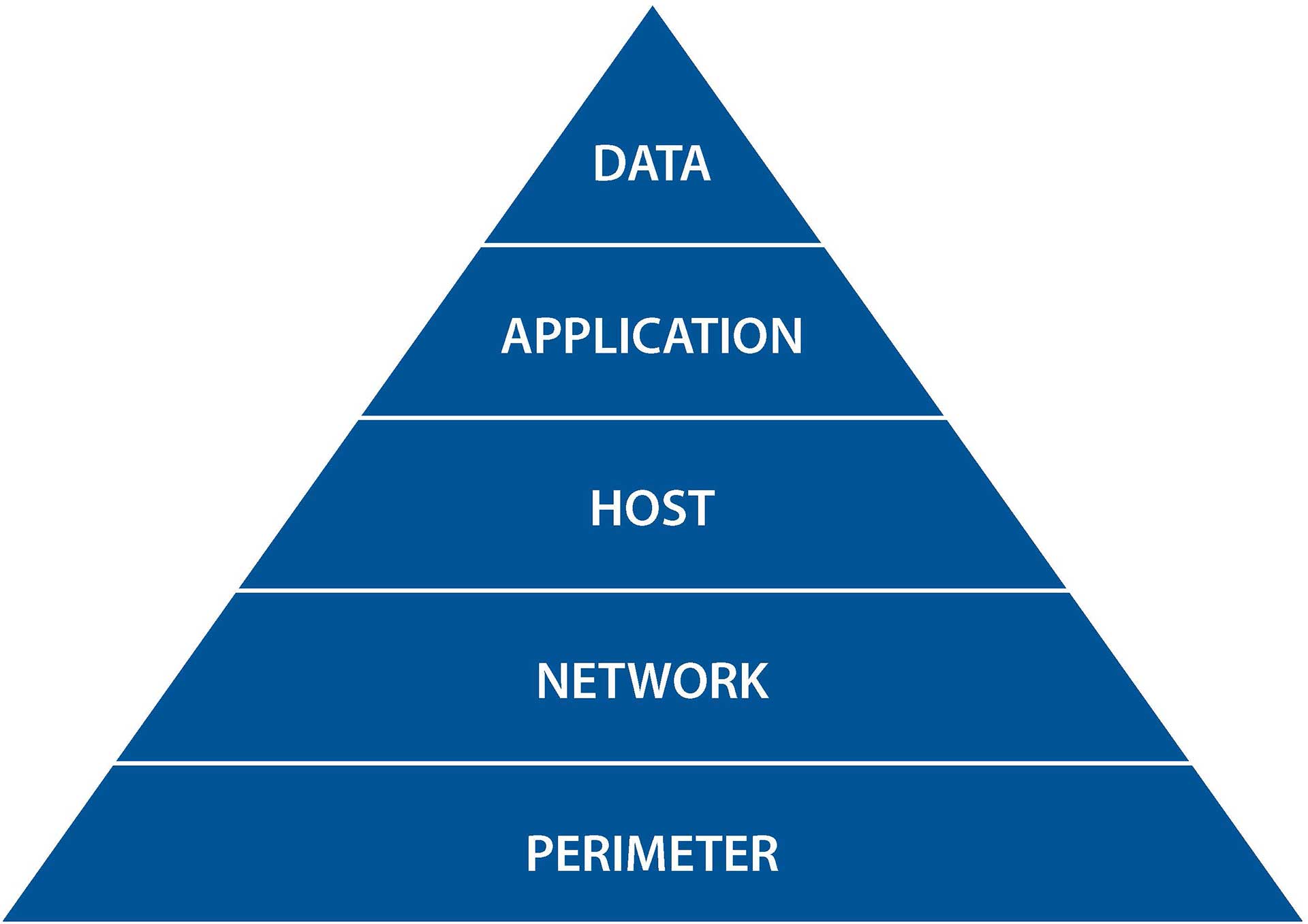
Security layers in automation systems
Lifecycle solutions
Digital security must consider human, organisational process and technology aspects. Networking and cooperation between the various players, as well as ongoing developments must also be considered. Networking enables the transfer of data and thus the improvement of situation awareness. Situation awareness is crucial in the event of an attack, or while preparing for an attack that is still preventable. Continuous development is also important because digital security is a highly dynamic area and hackers always strive to stay one step ahead.
In its most comprehensive form, digital security creates a lifecycle model. The lifecycle solution proceeds in stages: definition, analysis, design, implementation, review and continuous development. A lifecycle solution enables better resilience, whereby ICS security is maintained as a stand-alone process among other company processes.

Progress of an attack
An attack can be divided into four phases. The first phase is targeting, where the attacker develops situation awareness.
The next step is to perform a target analysis, which involves situational understanding. The third phase involves selecting the target and the attack method. In the last phase, the attack is carried out. After the attack, one can return to step 1 and execute a new attack based on the new situation awareness.
Attacks can be carried out in parallel, quickly disrupting multiple targets at the same time. The goal is to strategically paralyse the target. In this case, it is difficult for the party being attacked to develop good situation awareness and to systematically defend itself to avoid damage. Attacks sometimes only last a few minutes but can take years to prepare. In this case, it is important to detect potential reconnaissance operations against the company before the attack.
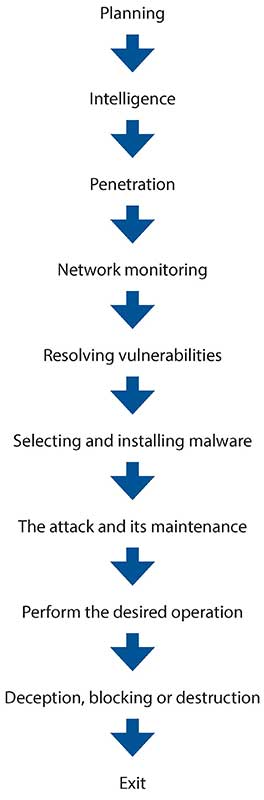
Typical steps in a cyber attack
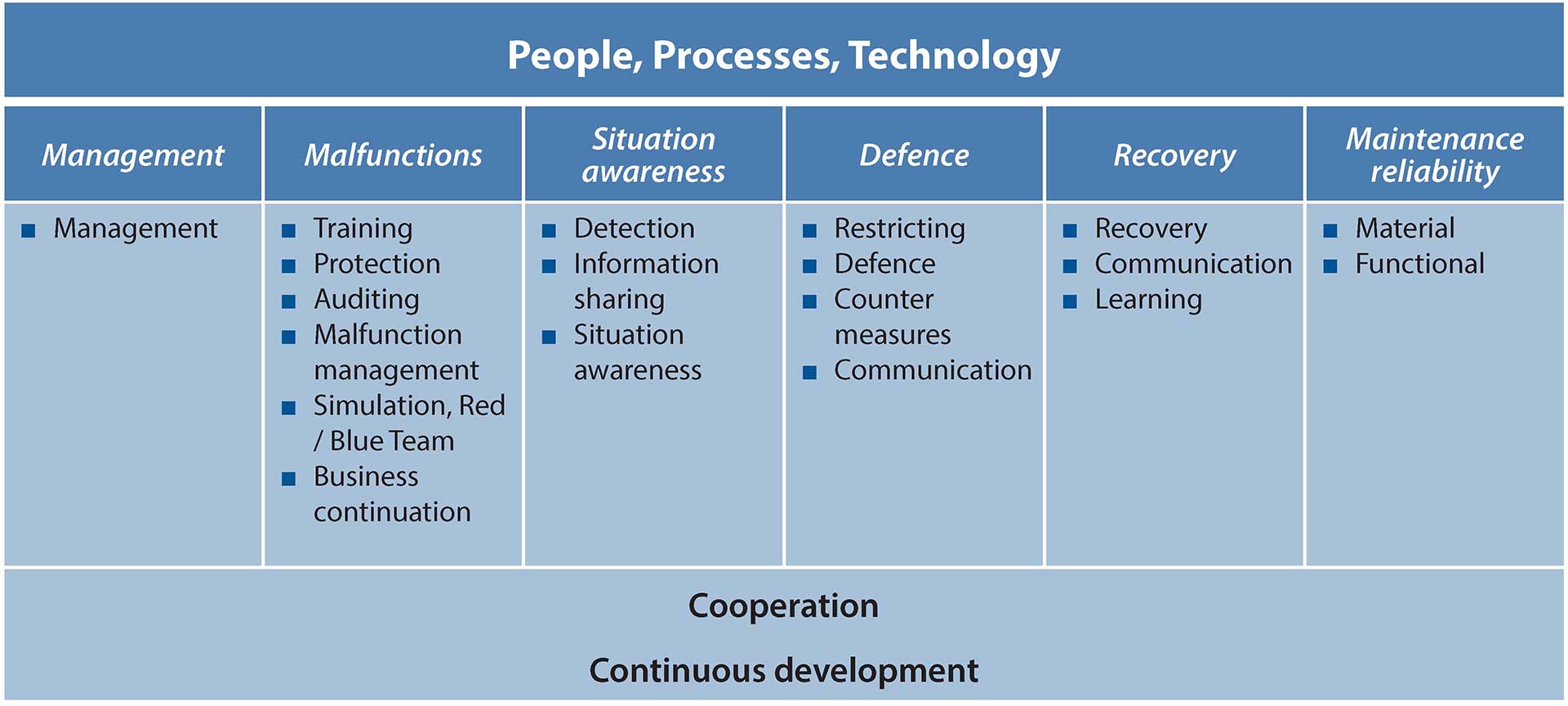
Table 2. Attack handling from the target’s perspective
SAFESCAN digital security vulnerability assessment process
SAFESCAN is a digital security vulnerability assessment process developed by Elomatic, which looks for vulnerabilities in an ICS system and associated risks. The process is subject to standards developed by the NIST Agency. The output of the process is a list of vulnerabilities and operations that should be performed to further improve the digital security of the system.
With SAFESCAN, one can easily and cost-effectively assess the vulnerabilities of an industrial automation system. At the beginning of the survey, the consultant becomes familiar with the customer’s automation system. The automation system is subdivided into parts, and these parts are examined from a digital security viewpoint by scoring the risk of each part by attribute.
The SAFESCAN product divides the automation system into five different levels. Solutions have been defined at the different levels to enhance the digital security of the system. Each of these levels creates a barrier for hackers and makes it harder to gain access. SAFESCAN is designed to prevent disruptions but is also prepared for disruptions and the need to restore business operations.
When investigating vulnerabilities, the customer’s staff is consulted. The discussions are preceded by training on the basics of digital security. After the training, discussions are conducted separately in small groups or between two persons. The discussions aim to maximise interaction in order to detect vulnerabilities.
At this stage, the discussions do not aim to identify solutions but to find out how digital security is dealt with in the company. Generally, the idea is to find out how the staff work and whether they have any suggestions for improvement.
Following the discussions, a summary and table showing the current vulnerability profile of the ICS system is prepared. Based on the vulnerability profile, control measures are proposed to improve digital security. In addition, a vulnerability profile is created after the control measures. This profile shows the impact on digital security (risk) if the proposed control measures are performed. Finally, a list of control measures that should be taken is drawn up.
A SAFESCAN analysis can also be performed periodically to check for new vulnerabilities and to make corrections to the risks identified in the previous inventory. This keeps the digital security of the target’s ICS system up to date.

This article was first published in Elomatic’s Top Engineer magazine 2/2019